
Yesterday, a Reuters photographer captured a photo of the freshly-ousted former National Security Advisor Mike Waltz checking his Signal messages during a Trump cabinet meeting. If you're not familiar…
Yesterday, a Reuters photographer captured a photo of the freshly-ousted former National Security Advisor Mike Waltz checking his Signal messages during a Trump cabinet meeting. If you're not familiar with Waltz, he's most well known for inviting The Atlantic's editor-in-chief to secret Trump administration war crimes Signal group. They discussed, and executed, bombing an urban apartment building full of civilians to kill a single man.
404 Media journalist Joseph Cox published a story pointing out that Waltz was not using the official Signal app, but rather "an obscure and unofficial version of Signal that is designed to archive messages" called TM SGNL.

This app uses Signal's servers, making it possible for Waltz to send end-to-end encrypted messages to normal Signal users, like Jeffrey Goldberg from The Atlantic, for example. However unlike the Signal end of the encrypted conversation, the TM SGNL end automatically archives a copy of the plaintext messages (even ones with disappearing messages) somewhere else that may or may not be secure.
In a video the company published, they show Signal messages getting archived into a Gmail account.
I decided to look into this app. I discovered:
- The senior executives of the company behind TM SGNL appear to be Israeli, and the CEO's bio mentions his work with Israel Defense Forces' Intelligence unit.
- TM SGNL is most likely violating Signal's open source license, and the company's other apps are probably violating the proprietary licenses of other software like WhatsApp and WeChat.
- The Android and iOS versions of the app are not available for the public to download, and in fact practically the only way to get the app is if you're using a device enrolled in an MDM service that's tied to an Apple Business Manager or Google Enterprise account.
- I speculate about exactly how I think the Trump administration is using this (unapproved for classified info) app to discuss classified info, and how they are likely managing their fleet of iPhones.
- Finally, I share a PDF and a video I discovered that go into detail about, among other things, where the chat logs may be stored.
Before I get started, consider subscribing to get these posts emailed directly to your inbox. If you want to support my work, considering becoming a paid supporter.
The company behind TM SGNL
The TM SGNL app is part of a suite of apps by a company called TeleMessage, which is owned by Smarsh, a company that makes e-discovery software, which is basically software designed for police and lawyers and whatnot to search archives of data.
I haven't spent a lot of time looking into TeleMessage, but what I did find at a quick glance is that several of the executives on the teams page list Israeli universities in their bios, and the CEO, Guy Levit, says that, "From 1996 until 1999, Guy served as the head of the planning and development of one of the IDF’s Intelligence elite technical units."
How the app probably works
Based on the photo of Waltz's screen, TM SGNL is most likely a version of Signal that is slightly modified. The app name is changed from "Signal" to "TM SGNL" (which is why Walt'z screen says, "Verify your TM SGNL PIN" instead of "Verify your Signal PIN").
And there is most likely an additional piece of code that gets executed whenever a message is sent or received which forwards the plaintext version of that message to the "corporate archive," as the company calls it.
TM SGNL might be violating Signal's open source licenses
Signal is open source. Here's the Signal-iOS code and here's the Signal-Android code. Because the code is available, creating an app like TM SGNL would actually be pretty easy to do.
Signal has done all of the hard work in making an end-to-end encryption messaging app. Signal also runs the server infrastructure. The TeleMessage devs simply have to clone the git repos of the client apps, figure out where to insert the archiving code, and make their own separate releases.
The Signal apps are licensed under the GNU Affero General Public License, a copyleft license that allows anyone to make modified versions (like TM SGNL) provided that they also use the same open source license. The license text says that when making modifications to the source code:
You must license the entire work, as a whole, under this License to anyone who comes into possession of a copy.
So, if someone has a copy of TM SGNL, they should be able to request that TeleMessage provide a copy of the source code, which should also be open source, and if TeleMessage does not comply they will be violating Signal's license – essentially, selling pirated software.
TeleMessage also publishes similar apps for WhatsApp, Telegram, and even WeChat, that probably work in similar ways. But because these apps are proprietary, I can't see any way that they're not violating the copyright on that app.
If I can find a copy of the TM SGNL app, I can not only request the source code, I could also try reverse engineering the app itself to see exactly how it differs from the official Signal app...
Trying to download the app
While I know Mike Waltz is using an iPhone, I'd actually prefer to get my hands on the Android version of TM SGNL simply because it's easier to crack open and look at its insides. But I'd settle for the iPhone version.
On the downloads page, TeleMessage lists two ways to install TM SGNL for Android and three ways to install it for iPhone.
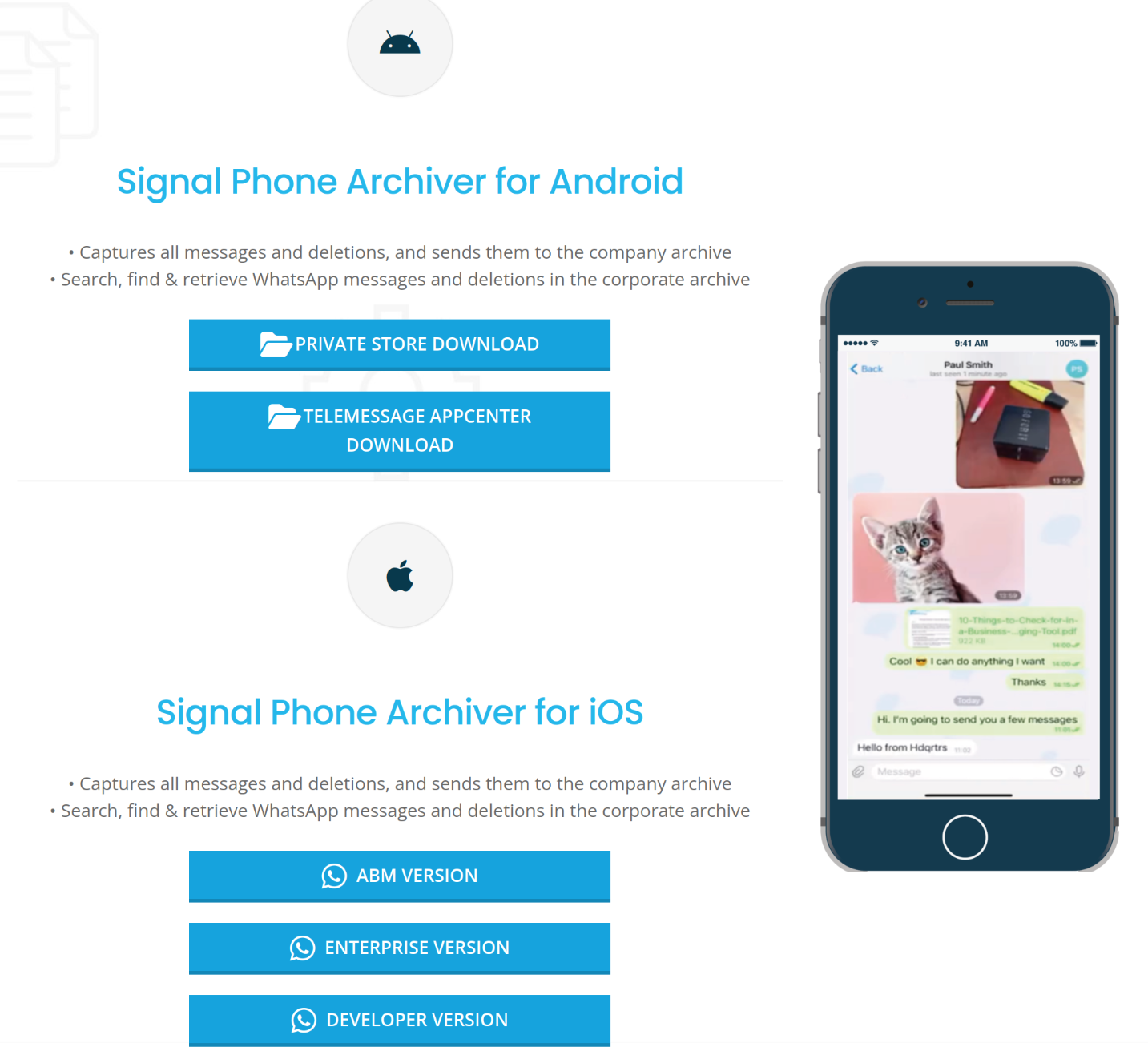
TeleMessage doesn't publicly distribute these apps in the Android Play Store or the iPhone App Store. So it's not as easy is just going and installing the app.
Android
The Private Store Download button links to documentation for allowing members of a Google Enterprise organization to download the app from Google's Private Store.
Basically, if your company uses Google Enterprise for device management, and your employees use Android devices, you can get TM SGNL added to a private part of the Play Store for your employees to download.
The instructions say to, "Copy your company’s Organization ID and email it to your TeleMessage project / account manager." This means that someone at TeleMessage needs to allow your organization to access the app. So, it looks like I'm not going to find a public download here.
The TeleMessage AppCenter Download button links just redirects back to the downloads page, so it doesn't actually work.
No luck. Let's try the iPhone version.
iOS
The ABM Version button links to docs explaining how companies can distribute apps to their staff using the Apple Business Manager.
Just like with Google Enterprise, if you want to give your employees access to the TM SGNL iPhone app, you need to share your ABM organization ID with TeleMessage, and then your account will gain access to a custom app which you can deploy to your employees. I'm not going to find a public download link here.
The Enterprise Version and Developer Version buttons link to docs explaining how to distribute the iOS app using either the Apple Developer Enterprise Program (used by big businesses to distribute custom or proprietary apps to their staff) or the Apple Developer Program (used by anyone who develops Mac or iOS apps – I have one of these accounts). In both of these options, the instructions include giving a TeleMessage account permissions in your Apple Developer account, allowing them to build and deploy versions of TM SNGL into your account. I won't find a public download link here.
Microsoft App Center
I had exhausted all of the options on the downloads page, but there was one more way to maybe get my hands on a copy of the app.
The TeleMessage website is incredibly sloppy. iOS links bring you to Android docs. A lot of the content seems to be old and out of date, but still public. Part of the sloppyness includes this page, called "Signal Capture Android Installation / Upgrade." I decided to use this sloppyness to my advantage.
This page instructs the user to:
- Allow installing apps from unknown sources. By default in Android, users can only install apps from the Play Store. By digging into the settings, you can allow installing apps from other app stores (like F-Droid), or by downloading APKs from websites.
- From your Android device, navigate to
https://www.telemessage.com/installsgapctrandroidand download and install the APK for TM SGNL.
This looked promising. In order to run this in Android, I installed Android Studio and spun up an Android emulator to load this URL in, but unfortunately it didn't work.
The URL https://www.telemessage.com/installsgapctrandroid redirects to https://install.appcenter.ms/users/tmwhatsapp/apps/telemessage-signal-android/distribution_groups/external, which should have allowed me to download the APK. But when I loaded it, I got this error message:
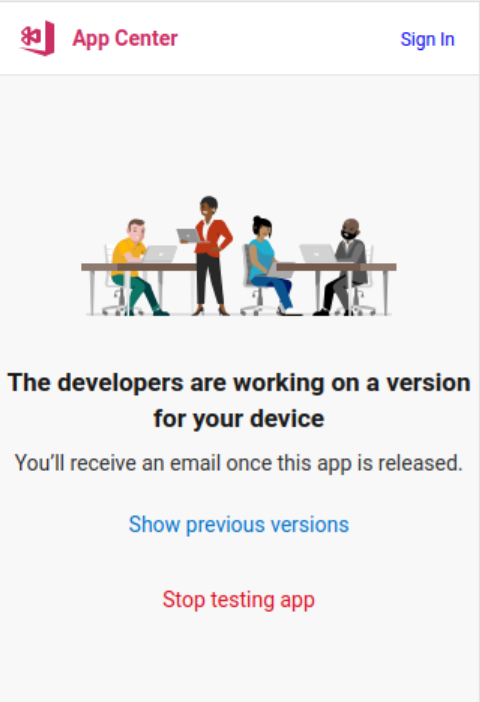
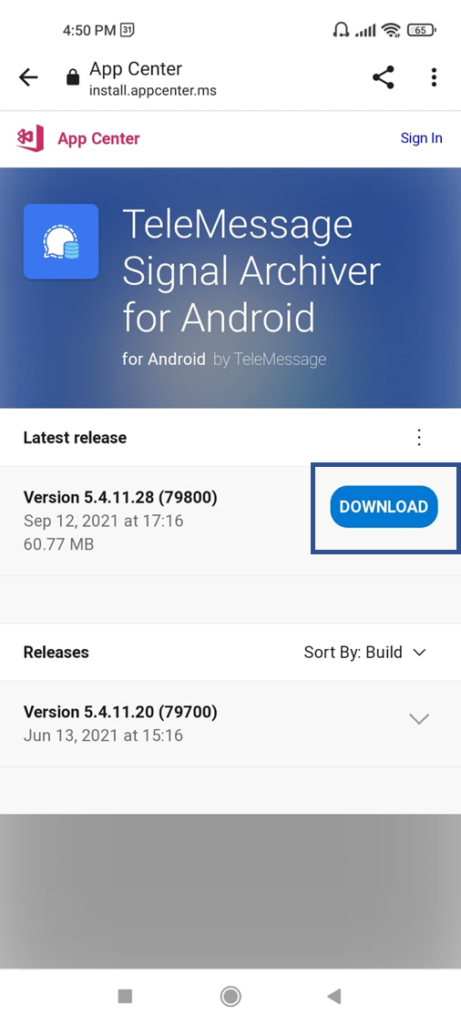
According to the docs, it should look like this:
To investigate further, I spun up Burp Suite – excellent software that allows you to inspect all of the HTTP requests a browser is making – and loaded the App Center URL.
Using Burp Suite, I discovered that the browser loads /api/v0.1/apps/tmwhatsapp/telemessage-signal-android/distribution_groups/external/public_releases, which return a JSON object containing a list of TM SGNL versions:
[
{
"id": 20,
"short_version": "7.36.2.10",
"version": "152900",
"origin": "appcenter",
"uploaded_at": "2025-03-16T15:42:35.547Z",
"mandatory_update": false,
"enabled": true,
"is_external_build": false
},
{
"id": 19,
"short_version": "7.27.1.7",
"version": "149800",
"origin": "appcenter",
"uploaded_at": "2024-12-26T07:38:42.175Z",
"mandatory_update": false,
"enabled": true,
"is_external_build": false
},
{
"id": 18,
"short_version": "7.18.0.5",
"version": "146800",
"origin": "appcenter",
"uploaded_at": "2024-11-25T13:00:26.541Z",
"mandatory_update": false,
"enabled": true,
"is_external_build": false
},Unfortunately this JSON object doesn't include URLs for APK files. I spent a bit of time digging into the now-defunct App Center docs, figuring out if there's a way to recover the APK URL. Alas, I came up short.
Mike Waltz, and presumably other senior Trump officials, are probably using managed iOS devices
As you can see in the photo, Mike Waltz uses an iPhone. And as I explored above, there are only a few ways to install TM SGNL onto iPhones. The simplest and most likely way is that his iPhone belongs to an Apple Business Manager account and is enrolled in MDM (remote management) service.
I have some experience running Apple Business Manager accounts myself. In order to create one, you need a legal entity that has a D-U-N-S number, which is a unique identifier for companies, managed by Dun & Broadstreet.
<speculation>
The following is all speculation, but here's what I think:
- The senior Trump people have some sort of legal entity. It might be the White House itself, or Trump's campaign organization, or something else, who knows.
- They have an Apple Business Manager account and are using an MDM service to remotely manage Apple devices. This central server is able to enforce settings, install apps, remotely lock or wipe devices, etc. The admin who runs the MDM service (as well as its hosting provider) has a lot of control over these devices. If I were foreign intelligence, this would be a primary target for me.
- The high level fascists in Trump's government, like Mike Waltz, Pete Hegseth, JD Vance, Tulsi Gabbard, etc., all have iPhones that are managed by this MDM service. They all use TM SGNL, which was automatically deployed to their devices via the MDM service.
- TM SGNL is configured on their devices to archive all messages (whether or not they automatically delete) to some central location. Knowing the level of incompetence and disregard for protecting classified information, my guess is it's storing the data in a public cloud provider like AWS or Azure, or in an email provider like Google or Microsoft. If I were foreign intelligence, this also be a primary target. People who hack this company, or malicious employees, can probably access all of these logs that are full of classified conversations.
</speculation>
Hi, I'm Micah. I'm a coder, a journalist, and I help people stay private and secure.
No spam. Unsubscribe anytime.
Detailed documentation and a video for TM SGNL
If you click around through the sloppy TeleMessage website enough, you'll see plenty of links to URLs at https://docs.smarsh.com that say they contain up-to-date documentation. Clicking these leads you to a login page, so these docs aren't public.
However, I found this page which also links to a PDF version of the docs. I grabbed it before it's gone. Here is the 78 page PDF, with detailed documentation for TM SGNL, also known as Signal Capture:
Here's a brief tour of this document.
Where chat logs are stored
The docs start with showing admins for an organization how to login to the Admin Portal, which is hosted at https://secure.telemessage.com.
After logging in as an admin, the next step is to assign users to archive plans that include a source (an app like TM SGNL) and a storage destination "such as Microsoft 365, SMTP, and SFTP."
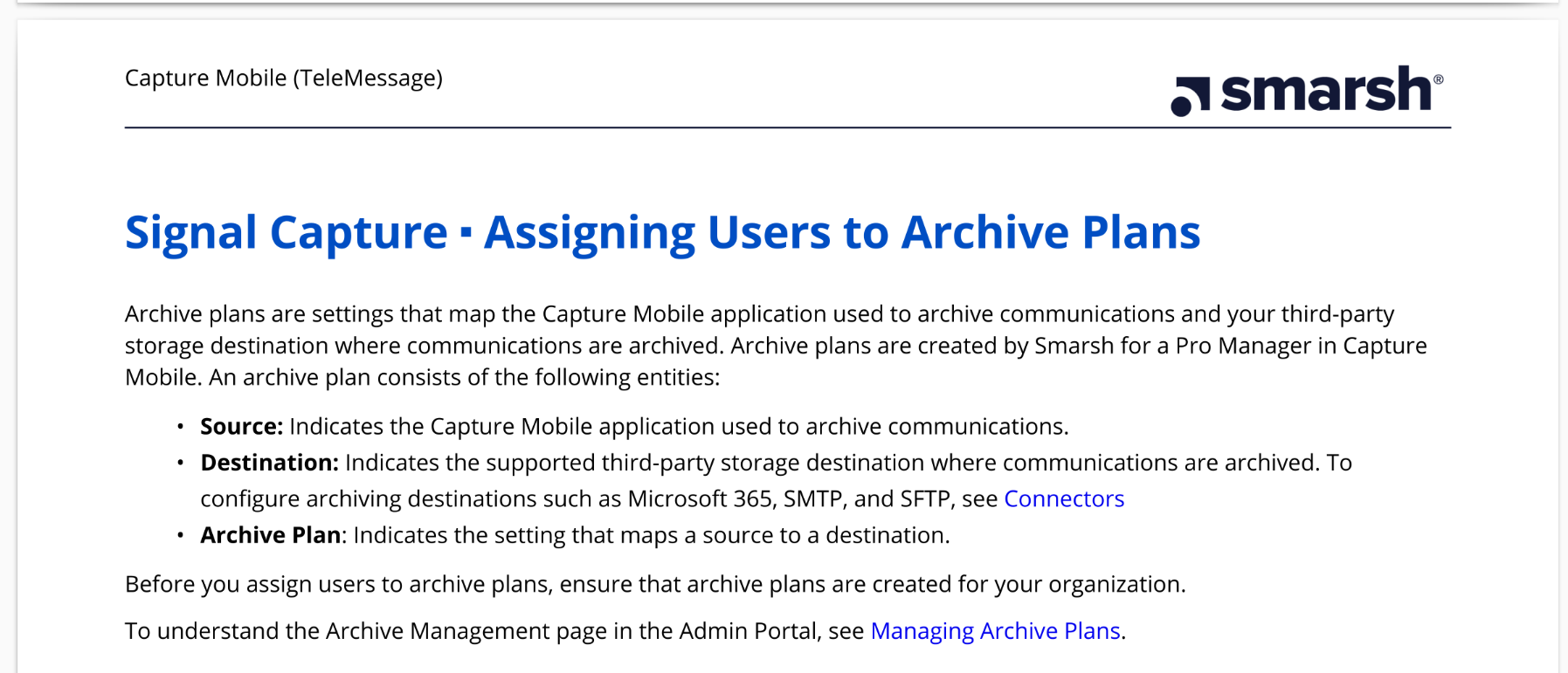
This gives a hint at the places where the classified Signal logs from senior Trump officials are likely stored. Microsoft 365 is Microsoft's suite of business services, and my guess is this refers to an Outlook email address. SMTP is an email protocol, meaning you can use any arbitrary email provider. And SFTP is a file transfer protocol, meaning you can store chat logs on arbitrary file servers.
The document includes a link to Connectors for more information, but unfortunately that links to a document behind a login page, so it's not public. This is all of the info I could find about where the chat logs are ultimately stored.
Assigning users to archive plans
The docs go on to explain how admins can assign different users (you know, people like Mike Waltz, Pete Hegseth, and Tulsi Gabbard) to archive plans. And this section even links to a publicly available (at least for now) video.
Here's a copy of the video, in case it disappears from where it's currently hosted:
Admin Portal - Adding a removing users from Archive Plans
While watching the video I noticed that, in addition to Signal, sources also include WhatsApp, Telegram, and even WeChat, which is the most popular messaging platform in China.
The destination for all archive plans in their test system is "Generic SMTP Archive," which really leads me to believe that most organizations will store archived data on an email server. This makes sense anyway, since email software has built-in features needed to search and investigate chat logs: support for threads that can contain two or more people, attachments, and robust search.
The narrator also mentions that Signal requires additional onboarding:
In the event that you have Signal or WeChat, there is some additional provisioning that is required from the Smarsh support side. So if you're going to be adding or removing users from Signal or WeChat, you will most likely need to be contacting Smarsh support to have the additional provisioning done on the backend.Signal users using iOS devices will need to be specifically provisioned by Smarsh support. And WeChat, all users that are going to be utilizing WeChat will have to be provisioned on the backend by support.
How the TM SGNL app is distributed for Android and iOS
In the "Distributing the Android Signal Application" section, the docs make it clear that only Google Enterprise Private Store is supported. There's a note pointing out that distributing the app via App Center is officially deprecated.

The "Distributing the iOS Signal Application" section is even more illuminating. It lists two methods, using Apple Business Manager (which I described above), and also an "unlisted app," which I'll talk about more below.
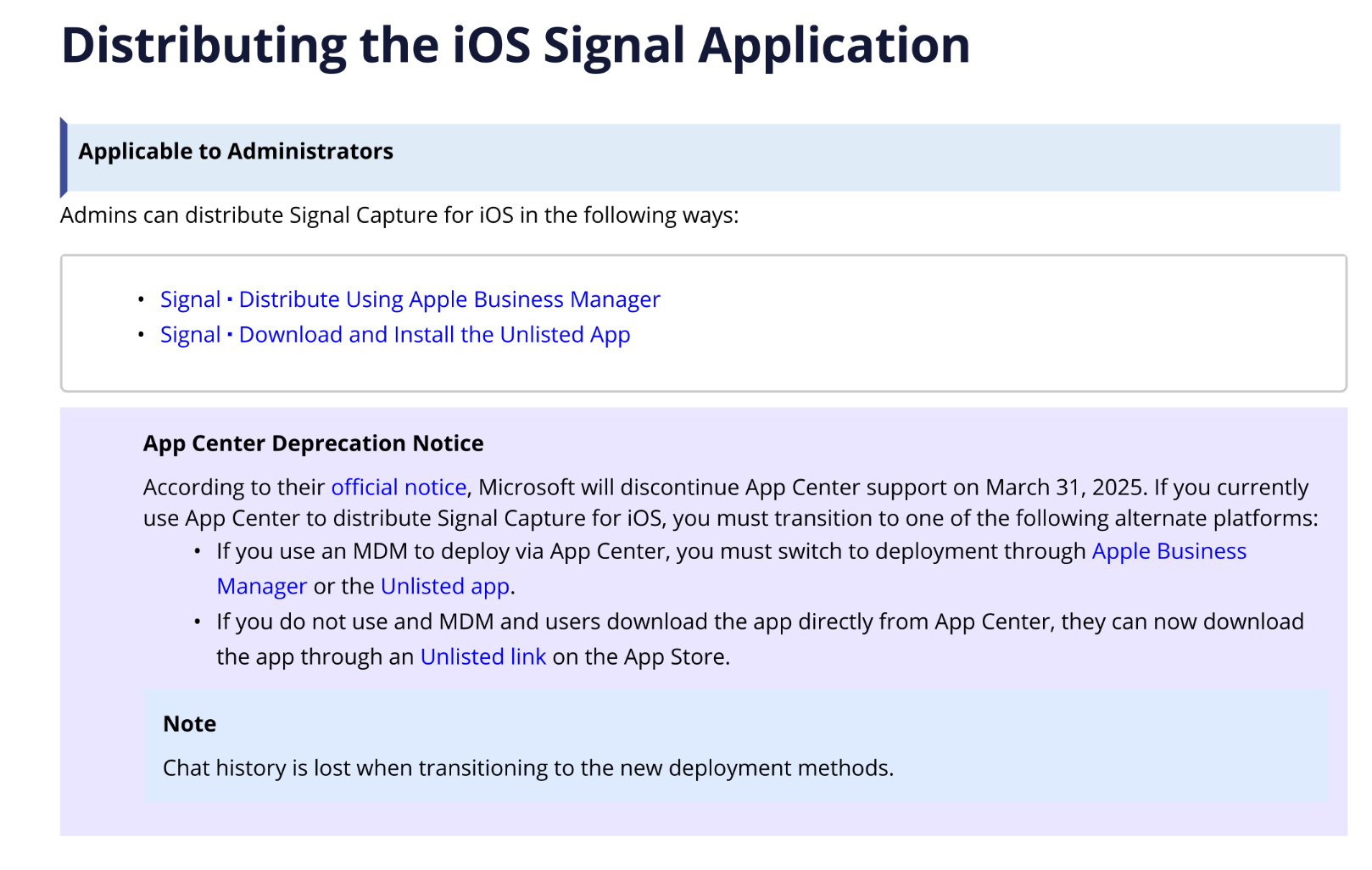
TeleMessage distributes the TM SGNL app directly in the App Store, but as an unlisted app. This means you can't find it by searching the App Store. You need the actual URL of the unlisted app in order to install it. The docs say:
Signal Capture for iOS is published as an unlisted app in the App Store. You will receive a Welcome email from Smarsh with a direct link to the unlisted app. You must open this link in your iPhone device.
I don't have any way of learning the URL of this unlisted app. But if you happen to know it, please let me know.
That's it for now!
If you found this interesting, subscribe to get these posts emailed directly to your inbox. If you want to support my work, considering becoming a paid supporter.
Read the original article
Comments
See also: "The Signal Clone the Trump Admin Uses Was Hacked" https://www.404media.co/the-signal-clone-the-trump-admin-use...
By croemer 2025-05-0513:38 See also https://news.ycombinator.com/item?id=43890179 for discussion of whether that article should count as a follow-up or SNI.
Normally I wouldn't link to meta discussion but this was such a weird borderline case that I spent over an hour trying to figure it out. Maybe that makes it interesting.
Edit: in case anyone's confused about the sequence here, micahflee posted the current thread 2 days ago. The timestamp at the top of this page is an artifact of us re-upping it (https://hn.algolia.com/?dateRange=all&page=0&prefix=true&que...).
FWIW, I never clicked into this when I originally saw it because I'm not that interested in a "technical analysis", but gained interest when the other title said that the app was hacked. To me, that's worth discussing, but here that lede is a bit buried. And I now only know about it because a friend sent me the link.
I do feel there's a pattern of me reading some interesting tech news, then thinking "wait, why didn't I see this discussed on HN?", to searching for it and finding a buried/flagged HN discussion due to it being somewhat tied to politics (what isn't?)
By myvoiceismypass 2025-05-0522:29 I have recently switched to the “active threads” feed which shows flagged content: https://news.ycombinator.com/active
By mycatisblack 2025-05-066:553 reply As a non-native English understander, I find it funny that discussions related to politics are “flagged”. I.e. carrying a flag.
By dragontamer 2025-05-0614:551 reply Someone carrying a flag is flagging.
Someone who had a flag applied to them was flagged.
Noun to verb conjugations are unofficial English. But we love verbing our words. Google has been verbed into Googling. And when someone is the target of Google we call that getting Googled.
It's again, unofficial and unwritten and unstudied American English. So don't sweat it. It's how our slang evolves. Apologies for the lack of consistency in our language!
By selenography 2025-05-0617:09 > It's again, unofficial and unwritten and unstudied American English.
Hm? Where'd you get that impression?
It's certainly unofficial -- English has no official governing body, so essentially _all_ English is unofficial. However, zero-derived denominal verbs are quite common in even formal written English [0], are well studied [1], and aren't at all limited to American English [2].
----
[0] As seen in this very thread.
[1] It took me almost no time to find a random academic paper [1a] and two Wikipedia articles [1b][1c].
[1a] https://dingo.sbs.arizona.edu/~hharley/PDFs/HarleyDenominalV...
[1b] https://en.wikipedia.org/wiki/Denominal_verb
[1c] https://en.wikipedia.org/wiki/Conversion_(word_formation)
[2] https://www.thetimes.com/uk/politics/article/the-pedant-noun...
Or "had a flag waved at them", like football assistant referees or F1 peoples.
By jon_richards 2025-05-0615:02 Or “called them over by raising a hand” with “flagged down”.
By batch12 2025-05-0617:27 I also read it as carrying a flag (applied by others) to highlight that it needs to be reviewed or hidden.
Imo it's a brand new thing so it deserves this technical analysis, the follow up also deserves its own post because of its both importance and political/security nature (government app attacked).
It would be if Google announced Gmail and there was a technical analysis and then it was hacked the same day, I would hope there would be a post for that.
See https://news.ycombinator.com/item?id=43896978 for why we didn't do that.
Short version: it's not possible to have separate discussions in the way you describe. They would just get totally blended.
I like your Gmail analogy but I don't think it applies here. The "technical analysis" article is driven by the same political/security concerns as the "hacked" update.
By mbreese 2025-05-0611:52 Thanks for adding the little bit of meta commentary here. I think it helps to understand a bit more about how the site functions. And with this case, particular, it is a very useful timeline to help follow the discussion.
By crazydoggers 2025-05-0614:391 reply This article doesn’t include information on the Hack.
The 404 media article linked in this article is an earlier article.
The 404 media article with the hack was posted last night at 6pm. So that needs a seperate post, and should not be marked duped.
By dang 2025-05-0620:37 I think I addressed all these points in https://news.ycombinator.com/item?id=43896978 and https://news.ycombinator.com/item?id=43901823, but if you read those and still have a question that isn't answered there, I can take a crack at it.
dang: the two posts are different topics, also isn't this one "show hn"? I'm so confused by the application of rules around self-posts.
By dang 2025-05-074:10 They are the same topic in the sense that the HN threads about them are going to lead to the exact same discussion. If you read https://news.ycombinator.com/item?id=43896978 and https://news.ycombinator.com/item?id=43901823, that should be clear - but if not, let me know and I'll try to clarify further.
"Show HN" is a separate thing entirely - it's true that the submitter of this article was the author (which is great), but that's not enough to make a post a Show HN (https://news.ycombinator.com/showhn.html).
By dang 2025-05-0617:39 Sorry! norome is correct. See https://hn.algolia.com/?dateRange=all&page=0&prefix=false&so...
By norome 2025-05-0613:29 significant new information
By computerthings 2025-05-0711:23 [dead]
Still trying to grasp the idea of archiving messages from E2E encrypted communication system into a storage that entirely breaks the purpose of using something like Signal.
It’s like encashing on the trust of Signal protocol, app while breaking its security model so that someone else can search through all messages.
What am I missing here?
> What am I missing here?
OK, say you're a bank. The SEC states you need to keep archives of every discussion your traders have with anyone at any time (I'm simplifying things but you get the point). You keep getting massive fines because traders were whatsapping about deals
So now you've got several options - you can use MS Teams, which of course offers archival, compliance monitoring etc. But that means trusting MSFT, and making sure your traders only use Teams and nothing else. You can use a dedicated application for the financial industry, like Symphony or ICE Chat or Bloomberg, but they're clunkier than B2C apps.
And then the Smarsh (owners of Telemessage) salesman calls you, and says "your users can keep using the apps they love - WhatsApp, Signal - but we make it compliant". And everyone loves it (as long as no-one in your Security or Legal teams are looking too hard at the implications of distributing a cracked version of WhatsApp through your MDM...)
Edit: here's the install document for their cracked WhatsApp binary https://smarsh.my.salesforce.com/sfc/p/#30000001FgxH/a/Pb000...
By JumpCrisscross 2025-05-0517:531 reply > say you're a bank. The SEC states you need to keep archives of every discussion your traders have with anyone at any time
These records are encrypted in storage.
By Etheryte 2025-05-0518:52 That is more than overly optimistic given how slow the pace of any technical innovation in finance is. The recent and not so recent issues with Citi are a good example of that.
By protocolture 2025-05-058:572 reply Seems like it doesnt resolve the trust issue it just shifts it to a smaller firm with more to lose.
By namdnay 2025-05-059:02 It definitely doesn't resolve the trust issue! I would trust MSFT a million times more than these cowboys. What it does give you is peace with your traders (who can be real divas..) - they can keep using "WhatsApp" and "Signal" and you can monitor everything
By 9cb14c1ec0 2025-05-0611:391 reply Oh wow! There are other ways to archive whatsapp messages that don't involve modified WhatsApp apks. Meta lawyers do not take kindly to modified WhatsApp apks.
> There are other ways to archive whatsapp messages that don't involve modified WhatsApp apks.
What other ways are there that don't involve WhatsApp's Google Drive backup feature or scraping the web interface?
The clean way to do it (which is how Telemessage’s competitors do it) is to use WhatsApp business APIs with dedicated phone numbers.
By stackskipton 2025-05-0614:182 reply Most traders I dealt with want to do it on personal cell phone so they can keep contacts as they move around. Most of them are like salespeople, they know exactly how much money they bring in and successful ones refuse to do anything that will impede THEIR method of working. SEC Fines, Regulations? Those are for less successful people.
EDIT: There was another post calling them divas, alot of them act that way.
By namdnay 2025-05-0615:32 yes, that's why TeleMessage managed to sell such a hacky solution - there was a clear desire for that product
By pcthrowaway 2025-05-076:511 reply I mean if they're going to use their personal devices for this then a cracked Whatsapp wouldn't help the business anyway.
For devices the company controls they can of course use the API the above poster mentioned though
By stackskipton 2025-05-0715:31 Yes it does. They convince the traders to let them install MDM and take over the phone, WhatsApp/Telegram/Signal still works, the business gets the records and if they leave the trading firm, the phone gets wiped but traders can just reinstall Store versions, log back in and everything is back.
By 9cb14c1ec0 2025-05-0613:18 I had scraping the web interface in mind.
By amarcheschi 2025-05-0514:51 ok, this absolutely reminds me of using indian whatsapp mods years ago. stickers, more features, local and portable backups... wouldn't try that as a member of the government though
By homebrewer 2025-05-0515:054 reply Is it a coincidence that it reads almost exactly like SMERSH?
Probably coincidence. The founder of the company was named Stephen Marsh.
By jaegrqualm 2025-05-061:43 There's a point at which coincidence and opportunity meet.
By tomhowls 2025-05-0517:27 [dead]
Probably not. It's trendy to give edgy names to companies. See: Palintir.
By PicassoCTs 2025-05-069:331 reply And the name is not very edgy and a pretty exact mission description - it describes exactly what it grows from. Seeing stones aka cellphone data of everyone, collected, analyzed and turned into predictions for kings.
By PicassoCTs 2025-05-078:201 reply To be honest, the good guys - turned out to be pretty embarrassing too.
The whole "everyone thinks like us" delusion bought with the surplus of a good times window distributed all around and its still willing to return to this delusional state of affairs.
The obvious plot-holes they reveal when it comes to we do not discuss nature (the bugs in the human mind are all fixable with education) and we do not discuss nurture (all cultures are equal, and equally capable - disregard the evidence before your eyes).
You don't get to juggle and drop so many balls and do not massively loose confidence!
The rule of (finger in ears) "La-La-La" is over - the problem is- the right is a reactionary mess, that has no solutions, analysis and tools to exploit these weaknesses.
By bigbadfeline 2025-05-0722:49 > You don't get to juggle and drop so many balls and do not massively loose confidence!
You don't get to run all this circus if you don't intend to run it only as a circus. It's time to stop kidding ourselves that anybody mainstream is sincere and smart enough to move anywhere different from where they all are told to go.
Huh? If the goal is compliance, you wouldn't use something that's worse for compliance - which is why the Legal and Security wouldn't like it. If it helped with compliance, they'd love it! So the reason can't be compliance.
You can never control what I do on my device with the message received- I can make screenshots, or, if the app prevents that, take a picture of the screen.
The goal of signal is trusted end-to-end encrypted communication. Device/Message security on either end is not in scope for Signals threat model.
By colanderman 2025-05-0512:451 reply TM SGNL changes the security model from "I trust the people in the chat" to "I trust the people in the chat and also the company archiving the chat".
If you don't trust the people in your chat, they shouldn't be in your chat.
> If you don't trust the people in your chat, they shouldn't be in your chat.
I assure you, none of these people trust each other. Backstabbing is normal.
They're also likely using it to talk to foreign counterparts. Again, most of whom they don't trust a bit.
Encryption isn't just about "do I trust the recipient".
By colanderman 2025-05-0519:242 reply You are conflating levels of trust.
The trust level required with Signal is, "do I trust the people in this chat not to share the specific communications I am sending to them with some other party whom I do not want to have a copy".
There are many many situations where this level of trust applies that "trust" in the general sense does not apply. It is a useful property.
And if you don't have that level of trust, don't put it in writing.
TM SGNL changes the trust required to, "do I also trust this 3rd party not to share the contents of any of my communications, possibly inadvertently due to poor security practices".
This is a categorical and demonstrably material difference in security model. I do not understand why so many are claiming it is not.
>TM SGNL changes the trust required to, "do I also trust this 3rd party not to share the contents of any of my communications, possibly inadvertently due to poor security practices".
That's the same level of trust really. Signal provides a guarantee that message bearer (i.e. Signal) can't see the contents, but end users may do whatever.
You can't really assume that counterparty's device isn't rooted by their company or they are themselves required by law to provide written transcripts to the archive at the end of each day. In fact, it's publicly known and mandated by law to do so for your counterparty that happens to be US government official.
The people who assume that they are talking with one of the government officials and expect records not to be kept are probably doing (borderline) illegal, like talking treason and bribes.
No, this is not a "nothing to hide argument", because those people aren't sending dickpics in their private capacity.
By yorwba 2025-05-0613:08 If your counterparty is compromised, that still only leaks your communication with that counterparty, but not other, unrelated conversations.
By philipwhiuk 2025-05-0520:22 > This is a categorical and demonstrably material difference in security model. I do not understand why so many are claiming it is not.
Because all it takes is one user to decide they trust the third party.
Right now you actually have to do more than trust everyone, you have to trust everyone they trust with their chat history. Which already can include this sort of third party.
One of the most popular “e2ee” communication systems, iMessage, does exactly this each night when the iMessage user’s phone backs up its endpoint keys or its iMessage history to Apple in a non-e2ee fashion.
This allows Apple (and the US intelligence community, including FBI/DHS) to surveil approximately 100% of all non-China iMessages in close to realtime (in the usual case where it’s set to backup cross-device iMessage sync keys).
(China, cleverly, requires Apple to not only store all the Chinese iCloud data in China, but also requires that it happen on machines owned and operated by a joint venture with a Chinese-government-controlled entity, keeping them from having to negotiate continued access to the data the way the FBI did.)
https://www.reuters.com/article/us-apple-fbi-icloud-exclusiv...
Yet Apple can still legitimately claim that iMessage is e2ee, even though the plaintext is being backed up in a way that is readable to them. It’s a backdoor by another name.
Everyone wins: Apple gets to say E2EE, the state gets to surveil the texts of everyone in the whole country without a warrant thanks to FISA.
By nearbuy 2025-05-0519:54 I suppose if both you and the recipient have cloud backups disabled, then Apple can no longer view your messages.
But outside of that scenario, is there any advantage to iMessage using e2ee instead of just regular TLS?
Edit: Apparently it's up to you whether you want your iCloud backups to use e2ee. There's an account setting: https://support.apple.com/en-us/102651. Standard protection is a sensible default for regular who aren't tech-savvy, as with e2ee they're at risk of losing all their iCloud data if they lose their key.
By watermelon0 2025-05-0519:582 reply That's an old article. According to Apple docs, Advanced Data Protection covers Device and Messages backups, which means they are E2EE.
Correct, but nobody turns it on because it’s opt in, and even if you turn it on, 100% of your iMessages will still be escrowed in a form readable to Apple due to the fact that the other ends of your iMessage conversations won’t have ADP enabled because it’s off by default.
Again, Apple gets to say “we have e2ee, any user who wants it can turn it on” and the FBI gets to read 100% of the texts in the country unimpeded.
If Apple really wanted to promote privacy, they’d have deployed the so-called “trust circle” system they designed and implemented which allowed a quorum of trusted contacts to use their own keys to allow you to recover your account e2ee keys without Apple being able to access it, rolled that out, and then slowly migrated their entire user base over to e2ee backups.
They have not, and they will not, because that will compromise the surveillance backdoor, and get them regulated upon, or worse. The current administration has already shown that they are willing to impose insanely steep tariffs on the iPhone.
You can’t fight city hall, you don’t need a weatherman to know which way the wind blows, etc. The US intelligence community has a heart attack gun. Tim Apple does not.
Separately it is an interesting aside that Apple’s 1A rights are being violated here by the presumptive retaliation should they publish such a migration feature (software code being protected speech).
And yet, it's somehow so effective that it's illegal in the UK because it doesn't let the government read everyone's messages.
By Terr_ 2025-05-0521:31 TBF, governments trying to outlaw some kind of privacy doesn't necessarily mean it's a current impediment to them. They can be planning ahead, securing their position, or just trying to move the window of what is considered acceptable.
Are there any stats as to the percentage of iPhone users that enable Advanced Data Protection? Defaults matter a lot, and I wouldn't be surprised if that number is (well) below 10%.
If you are the only person out of all the people you correspond with who has ADP enabled, then everyone you correspond with is uploading the plaintext of your messages to Apple.
By sneak 2025-05-060:07 The number is well well below 1%. I would bet six figure sums it is below 0.1%.
Effectively nobody has it on. 99%+ of users aren’t even aware of the feature’s existence.
https://daringfireball.net/linked/2023/12/05/icloud-advanced...
You have to remember that there are something like a billion+ iOS users out there. 100 million people have not written down their 27 character alphanumeric account recovery key.
By nicce 2025-05-0521:46 The same applies to WhatsApp. Messages backups are unencrypted by default and even the whole iPhone backup includes the unencrypted chat history of WhatsApp by default. One reason why it was a big deal for UK to disable iCloud’s E2EE backup.
There are compliance reasons where you want the communications encrypted in flight, but need them retained at rest for compliance reasons. Federal record keeping laws would otherwise prohibit the use of a service like Signal. I'm honestly impressed that the people involved actually took the extra effort for compliance when nothing else they did was above board...
> There are compliance reasons
Makes sense. But still debatable if the compliance requirements are acting against the security model or perhaps there are biggest concerns here than just secure communication.
By actionfromafar 2025-05-057:301 reply I would not assume the archives were meant for compliance and federal records.
By ceejayoz 2025-05-0510:31 We also have no evidence it was in use back in March. It may be a response to that oops.
Any client-side limitations are not part of the security model because you don't control other people's devices. Even with an unmodified app, they're trivially bypassed using a rooted/jailbroken device.
By colanderman 2025-05-0512:472 reply Not part of Signal's security model, but trusting people in that chat very much can and should be part of the user's security model. If you don't trust them, why are they in the chat in the first place?
By barryrandall 2025-05-0513:541 reply It's not a person in the chat, it's an account. The account is usually controlled by the person associated with it, but you can't assume that it's always controlled by that person.
By philipwhiuk 2025-05-0520:23 Is it though? I think TM Signal is just emailing the chats to a server from the phone it's installed on.
> If you don't trust them, why are they in the chat in the first place?
Journalist? Taliban negotiator? Ex-wife?
By colanderman 2025-05-0519:081 reply You are conflating "trust in all ways" with "trust to receive the communications in the specific chat they are party to". The former is not relevant.
By Muromec 2025-05-0520:59 Well the ex-wife in question can be trusted to receive it a-okay and screenshot them to send to her lawyer and cops too, depending on contents. So do US government officials. Now we just know how exactly they do it.
By pmontra 2025-05-0519:10 Or with the more affordable (in terms of skills) method of using another phone to take pictures of key messages on the screen of the first one.
By rkuykendall-com 2025-05-0819:53 OK, say you're a bank. The SEC does not care what you do and is actively working to make sure nobody else does either. You never get fines and all the traders are whatsapping about deals and it's awesome. But what if the FEC decides to care in the future? Just mark all your messages as self-deleting. But what if you want to be able to read them in the future?
And then the Smarsh (owners of Telemessage) salesman calls you, and says "your users can keep using the apps they love - WhatsApp, Signal - but we archive the self-deleting messages somewhere you can hide from the SEC if they happen to change their mind". And everyone loves it (you already fired all the Security or Legal teams).
By Spooky23 2025-05-0613:44 The purpose of using something like Signal is not compatible with the needs of the government or the law.
I’ve worked for non-Federal government. Your work product is not your own, and the public interest, as expressed by the law requires that your communications and decisions can be reviewed by the government you serve.
The US government created the dark web to enable espionage — its pretty obvious why they need to read their employees mail.
By jowea 2025-05-0521:34 My guesses:
You want to talk to people who want to use Signal, but you yourself don't care about E2E
You trust Telemedia, but not Telegram, or Meta. And you want convenient archiving.
By catlikesshrimp 2025-05-0518:10 Maybe someone wanted to please the procedure of law but also had to please the bros. The result is a hack of a secure program that adds conversation archiving.
By SequoiaHope 2025-05-067:421 reply My wild speculation is that someone wants to use AI to monitor everyone’s communication.
What they should have done is write a bot that you invite to every conversation for "archival purposes". No new app.
By danesparza 2025-05-0610:021 reply Then you have a new attack surface. It's still missing the point of signal.
By blitzar 2025-05-0610:23 If your institution has to log the messages, they are a third party to the conversation, I would rather they were "in the chat" than the lowest bidder third party.
A chat participant bot would also be handy if you wanted to feed everything through your Ai bot at the same time.
The big part of this story which nobody is talking about is the fact that the app is literally controlled by a bunch of “former” Israeli intelligence officers. Who now have what is arguably the worlds most valuable access out of anyone.
I don't think it's that big: USG procures defense and intelligence tech more or less constantly from Israel. It's unlikely that Israel would threaten that relationship (and the value they extract from it in terms of favorable relations) in exchange for military intelligence that's already shared with them.
(I feel like I have to say this in every thread that insinuates something sinister about being a "former Israeli intelligence officer": the structure of Israel's military and mandatory service is such that just about everybody with technical skills serves in some kind of "intelligence" capacity. It's not a very big country. This is, of course, independent from any normative claims about Israel's government, politics, etc. -- it's what you'd expect in any small country that has mandatory military service with a significant intelligence component.)
By like_any_other 2025-05-0518:411 reply > I don't think it's that big: USG procures defense and intelligence tech more or less constantly from Israel. It's unlikely that Israel would threaten that relationship (and the value they extract from it in terms of favorable relations) in exchange for military intelligence that's already shared with them.
Correct - they would not use that intelligence to threaten that relationship, but to maintain it. Knowing the political leanings of politicians and government officials (for example, identifying any that think that relationship is more of a cost than a benefit) is extremely valuable to that end.
The over/under there doesn't make sense: the US hasn't had a meaningfully hostile-to-Israel policy ever, so pervasively tapping some of the most sensitive USG communications would be a stunning risk to take with a very safe ally.
(It also beggars belief in the current climate -- I would be hard-pressed to name a single member of the current administration who hasn't yelled until purple in the face about their support for Israel's current government and wartime policies.)
By like_any_other 2025-05-0519:11 You might think so, but they didn't face any backlash for buying politicians [1,2] and bragging about it [3], so why would they worry? You also assume that the US is a "very safe ally" naturally, and not as a consequence of means such as these.
[1] After House Speaker Mike Johnson Pushed Through Israel Aid Package, AIPAC Cash Came Flowing In - https://theintercept.com/2024/01/20/israel-aipac-house-mike-...
[2] The Israel lobby and U.S. foreign policy - https://www.hks.harvard.edu/publications/israel-lobby-and-us...
[3] More than 95% of AIPAC-backed candidates won their election last night! Being pro-Israel is good policy and good politics! - https://x.com/AIPAC/status/1590362232915132417
By immibis 2025-05-0520:27 Everyone is tapping everyone else to the extent they can get away with it - especially allies, because they can get away with it more. You don't think the NSA monitors every single bit that flows in and out of the USA?
Periodically, someone gets caught red-handed, a fuss is made, some diplomats get thrown out and replaced with other ones, and then everyone continues doing it.
By iAMkenough 2025-05-0520:36 They have never had a hostile-to-Israel policy and never will because of the leverage Israel has over US politicians.
There's a reason the US bought this app from Israelis, and it wasn't because of improved security or archive compliance.
For how much they like to beat the "buy American" drum, this contradicts that.
By senderista 2025-05-0522:061 reply You'll note that this case caused exactly the kind of outcome I'm talking about: Pollard was an anomaly (to my knowledge, the only recorded case of a US citizen spying for a US ally) whose activities caused a massive intelligence break between US and Israel that lasted for years and probably did more damage than "good" it served for Israel's intelligence apparatus[1]. That kind of lesson is hard-learned and probably not forgotten, regardless of the fact that Pollard is a poster-boy in Israel's version of a culture war.
[1]: https://www.thedailybeast.com/israeli-spies-arent-exactly-re...
By pmyteh 2025-05-0611:05 Julius and Ethel Rosenberg were also US citizens spying for a US ally, at least in theory. Though the Soviet Union had stopped being an ally before they were convicted, of course.
By arandomusername 2025-05-0522:271 reply The most "hostile to Israel" policy was under JFK, which is interesting.
By woodruffw 2025-05-0522:50 Yep. In general there's been no truly "hostile to Israel" US president. The closest thing to "hostility" has been negotiating (under JFK, Carter, Bush Sr., and Obama most notably) with regards to one or more of Iran, the '67 border, WB settlements, etc. Israel has increasingly (and wrongly) considered these "meddling" under its far-right government, which is a internal change within their own politics rather than a marked change in the US's own tactics.
I’m saying this as someone who almost certainly has a lot more knowledge about intelligence and the US / Israeli relationship than you do.
While some of the points you make are indeed correct it actually paints an inaccurate overall picture.
For example: not widely known but 100% true, Israel is and has been for a long time classified as the highest level of counterintelligence threat to the US on par with China, Russia, Cuba and others.
I assure you, this is a big fucking deal and not something to be waved away with “everyone’s intel, don’t worry it’s probably nothing”.
By woodruffw 2025-05-0520:15 I'm not saying it's not a big deal. It obviously is.
I'm saying that the fact that it's Israeli tech is not itself the biggest part of the story.
By aucisson_masque 2025-05-0522:381 reply Israël have different interest than the usa.
Today they may collide in most instances, who's to say tomorrow it will still be the case. For instance when Iran gets the nuclear bomb and threaten Israel with it ?
An encrypted messaging system, used by the American government, is in my opinion even worst than the supposed Huawei 5g antenna data collection.
Huawei wouldn't have had access to secret talk between top government official, at least not decrypted.
By nozzlegear 2025-05-0614:081 reply >For instance when Iran gets the nuclear bomb and threaten Israel with it ?
I don't know if this was your intention, but it's exceedingly likely that the US would side with Israel in all circumstances if Iran threatened Israel with a nuclear weapon, no matter who is president. In fact, the threat of Iran attacking Israel was one of the key reasons† Biden refused to unilaterally stop all arms shipments to Israel.
† Source: War by Bob Woodward.
Given that Trump's foreign policy is quite alien compared to his predecessors, I don't know how valuable looking to the past is for this sort of thing. A new president, of any political bent, may follow the example and make further breaks with the past.
By nozzlegear 2025-05-0716:37 I agree for the most part, his foreign policy is very alien compared to Biden or any other "normal" president. When it comes to Iran and supporting Israel, though, I think he's still pretty hawkish and predictable for a Republican president (or as predictable as Trump can be). Remember during his first presidency, he withdrew from the Iran nuclear deal, then he imposed a bunch of tight sanctions on Iran while reinforcing ties with Israel and recognizing Jerusalem as its capital.
Part of his hawkishness toward Iran comes from the kinds of national security advisers he keeps (typically all hawkish on Iran themselves, with some exceptions like General Mark Milley), and part of it comes from his admiration for "strongman" leaders like Bibi.
I would absolutely put "Israel taps the National Security Advisor's phone" in a different category of risk to the two country's relationship than previous activities. This, again, isn't a normative argument.
(A piece of context that's often missing from - typically charged - discussions about US/Israel relationships is the degree of dependence between the two, and how that's varied over the years. Israel's defense policies have historically been informed by a desire to be fully self-sufficient during wartime, i.e. not require active support from countries like the U.S. That policy has been deprioritized over the last 20-30 years, to the point where the US is now a significant active defense provider for Israel, rather than just an arms supplier. This is a dependency relationship that's new to the ongoing conflict, and should color any analysis of Israel's willingness to do things that would threaten its relationship with the U.S.)
What makes you think it didn't already do so in the past and thus is a new thing? Allies spy on each other all the time.
I guess US gov would not like to have it be out publicly, but they must understand that this is being at least attempted and US likely does it to Israel, too.
https://www.timesofisrael.com/new-nsa-document-highlights-is...
By woodruffw 2025-05-0520:19 I'm sure they do. I would expect a little bit more, uh, flair to it than "you bought the spyware from us," though.
My point here is pretty narrow: I'm sure Israel spies on the US, and we spy on them. My only doubt is whether TM SGNL itself is an element of that, or whether it's just another flavor of junk software sold to USG to paper over the gaps between technology and compliance requirements.
By stackskipton 2025-05-0515:121 reply >Some minor spying would not even register.
I mean, they stole weapons grade Uranium from United States along with nuclear secrets and we just shrugged our shoulders: https://www.theguardian.com/world/2014/jan/15/truth-israels-...
By smashah 2025-05-061:20 [flagged]
The US and many other countries have been buying Israeli surveillance tools for years or decades.
I would hope that any message archiving is being done on an organization-owned server though.
By lysp 2025-05-055:50 > The US and many other countries have been buying Israeli surveillance tools for years or decades.
Yes, tools like Cellebrite and zero-day exploits.
Those are tools which are used to spy on people outside of the government.
This is a tool that has data created by the government.
> I would hope that any message archiving is being done on an organization-owned server though.
There's compelling evidence that the messages all pass through TM servers before being archived.
https://www.404media.co/the-signal-clone-the-trump-admin-use...
By userbinator 2025-05-055:031 reply There's compelling evidence that the messages all pass through TM servers before being archived.
The question is where the E2E encryption goes between.
The E2E encryption is likely not even relevant, unless I'm missing something?
The builds that are distributed would likely just send the plaintext un-encrypted message separately to the archive, and I'm guessing that means it goes right to TM servers before being dispatched elsewhere.
By Y_Y 2025-05-058:48 Ah yes, it's end-to-end alright, end-to-end cleartext.
I know it's pretty fun to do the espionage angle with this comment.
But is this really just evidence that a mandatory draft is actually good economic policy? Having a forced networking event where a bunch of similar skilled individual meet each other seems to be producing a ton of economic value for Israel.
By mdhb 2025-05-0519:40 This isn’t a one or the other thing. You’re just bringing up an unrelated point.
By Cthulhu_ 2025-05-0612:29 ? But in the US, people get the same - if not better - economic value from universities, or working together at the same companies, or being in the same spaces, or meetups, etc.
By freeamz 2025-05-080:38 >The big part of this story which nobody is talking about is the fact that the app is literally controlled by a bunch of “former” Israeli intelligence officers. Who now have what is arguably the worlds most valuable access out of anyone.
You are just talking about the clone, NOT signal foundation and the dev team?
By krunck 2025-05-0518:07 It's not like Israel doesn't already have the highest level of access to the administration's plans. Canada could be made the 51st state and Israel would still have more access to the Trump administrations plans. There is some sort of strong connection between the USA and Israel. What that is, I don't know.
By harrisrobin 2025-05-0317:131 reply [flagged]
> Israel’s grip on DC’s balls is far too strong
I more or less agree.
> We’re literally an occupied nation
The language of the US under occupation is a neonazi talking point, ZOG (Zionist Occupation Government) being a phrase neonazi morons like. Maybe a coincidence.
By anzjxbxkxkxb 2025-05-0614:09 [flagged]
By arandomusername 2025-05-0522:50 [flagged]
By smashah 2025-05-061:13 [flagged]
By ObliviousLib 2025-05-051:52 [flagged]
By Tabular-Iceberg 2025-05-0519:061 reply I don't like the association any more than you, but what's the greater threat to the United States, the capture of its congress, administration and intelligence community by a foreign power, or a ragtag group of politically and culturally irrelevant LARPers?
By uxp100 2025-05-0611:45 Honestly, I don’t think either is a true threat to the United States. I think that while Israel has been hugely influential the past 30 years, and had a close relationship longer on the intelligence front, that is far different than capture and occupation. Israel’s influence has been awful for the people of Iraq, Iran and Palestine, among others, but I don’t just disagree with the phrasing of occupation, I disagree with the premise. A significant part of why Israel gets so much of what it wants is because many of those in power in the US over the past 30 years like the role it plays in Middle East politics.
(I’ve been using 30 years due to feeling that HW Bush was stronger with Israel on the particular issue of Palestine, but really, not an expert here at all)